Aws S3 Security Checklist

As an aws customer you benefit from a data center and network architecture that are built to meet the requirements of the most security sensitive organizations.
Aws s3 security checklist. Helps organizations take into account the different features and services. Aws security checklist this checklist provides customer recommendations that align with the well architected framework security pillar. Assess your existing organizational use of aws and to ensure it meets security best practices. Today i ve read on infosec island this article by sanjay kalra focused precisely on s3 security with a useful security checklist.
3 encrypt inbound and outbound s3 data traffic. It defines which aws accounts iam users iam roles and aws services will have access to the files in the bucket including anonymous access and under which conditions. Monitoring of s3 buckets which have full control for authenticated group. Aws s3 security tip 2 prevent public access.
By john martinez. This evaluation is based on a series of best practices and is built off the operational checklists for aws 1. If you operate under those assumptions and use automation to continuously monitor your s3 security settings you ll be sure to find and fix your vulnerabilities faster than the bad actors can exploit them. Sanjay explain that often a customer moving from traditional enterprise can easily misread the meaning of the s3 access groups.
The auditing security checklist for aws can help you. Monitoring of s3 buckets which have full control for all users group. Below is the security monitoring checklist for aws s3. Some days ago i ve written about aws s3 security concerns with a post about some tools to find unsecured buckets.
Aws config provides a managed rule cloudtrail s3 dataevents enabled that you can use to confirm that at least one cloudtrail trail is logging data events for your s3 buckets. The most important security configuration of an s3 bucket is the bucket policy. Secure the cloud aws s3 prisma public cloud. Monitoring of s3 buckets which have default encryption disabled.
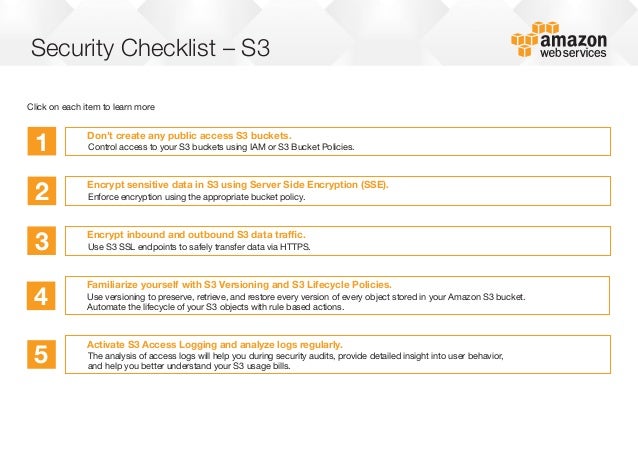
The checklist consists of three categories. Cloud security at aws is the highest priority. Evaluate the ability of aws services to meet information security objectives and ensure future deployments within the aws cloud are done in a secure and compliant way. Security checklist s3 click on each item to learn more 1 don t create any public access s3 buckets.
This aws security readiness checklist is intended to help organizations evaluate their applications and systems before deployment on aws. Identity access management 1. Your aws s3 bucket safety checklist. 2 encrypt sensitive data in s3 using server side encryption sse.
Control access to your s3 buckets using iam or s3 bucket policies. Use aws organizations to manage your accounts use the root user by exception with multi factor authentication mfa enabled and configure account. You should remove public access from all your s3 buckets unless it s necessary.